Knowledge Base
VPC Flow Logs Enabled
Risk level: Low
Rule ID: vpc-flow-log-check
- The Center of Internet Security AWS Foundations Benchmark
- Payment Card Industry Data Security Standard (PCI DSS)
- General Data Protection Regulation (GDPR)
- APRA
- MAS
- NIST 800-53 (Rev. 4)
Audit
01
Sign in to the AWS Management Console.
02
Navigate to VPC dashboard at https://console.aws.amazon.com/vpc/.
03
In the left navigation panel, select Your VPCs.
04
Select the VPC that you need to check.
05
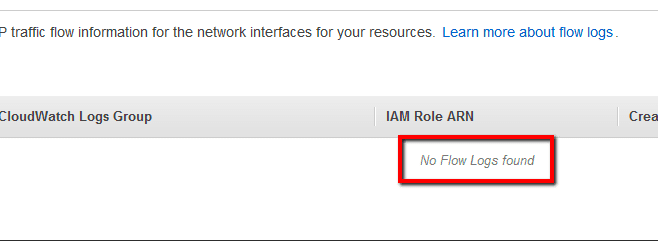
Select the Flow Logs tab from the bottom panel.
06
And search for any Flow Logs entries available for the selected VPC.
01
Run describe-vpcs command (OSX/Linux/UNIX) to list the VPC networks available in the current AWS region:
aws ec2 describe-vpcs
02
The command output should expose each VPC ID and its metadata:
{
"Vpcs": [
{
"VpcId": "vpc-f7ac5792",
"InstanceTenancy": "default",
"Tags": [
{
"Value": "MyWebVPC",
"Key": "Name"
}
],
"State": "available",
"DhcpOptionsId": "dopt-80e3f7e2",
"CidrBlock": "172.31.0.0/16",
"IsDefault": true
}
]
}
03
Run describe-flow-logs command (OSX/Linux/UNIX) using the VPC ID to determine if the selected virtual network has the Flow Logs feature enabled:
aws ec2 describe-flow-logs
--filter "Name=resource-id,Values=vpc-f7ac5792"
04
If there are no Flow Logs created for the selected VPC, the command output will return an empty list []:
{
"FlowLogs": []
}
Remediation / Resolution
01
Sign in to the AWS Management Console.
02
Navigate to IAM dashboard at https://console.aws.amazon.com/iam/.
03
In the left navigation panel, click Policies.
04
Click Create Policy button from the IAM dashboard top menu.
05
Select Create Your Own Policy and type a name and a description (optional) for the policy.
06
In the Policy Document field, paste the following custom IAM policy:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"logs:CreateLogGroup",
"logs:CreateLogStream",
"logs:PutLogEvents",
"logs:DescribeLogStreams"
],
"Resource": [
"arn:aws:logs:*:*:*"
]
}
]
}
07
Click Create Policy
08
In the left navigation panel, click Roles.
09
Click Create New Role button from the IAM dashboard top menu and follow the wizard:
- Enter a name for the IAM role.
- Under AWS Service Roles select Amazon EC2.
-
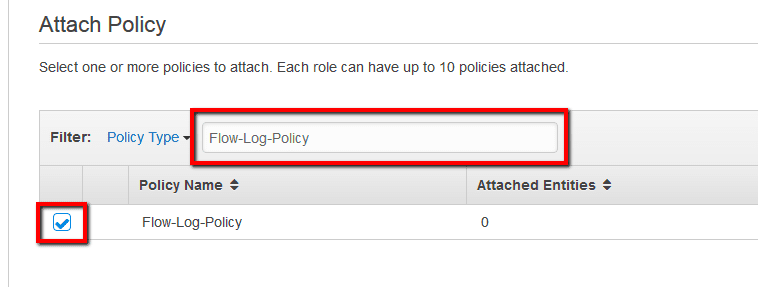
Search for the policy name created earlier and select it:
- Click Next Step
- Review the IAM role information and click Create Role
10
In the left navigation panel, click Roles.
11
Select the newly created IAM role.
12
Select Trust Relationships tab from the bottom panel and click Edit Trust Relationship.
13
Paste the following access control policy document and click Update Trust Policy tab from the bottom panel and click Edit Trust Relationship.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": "vpc-flow-logs.amazonaws.com"
},
"Action": "sts:AssumeRole"
}
]
}
01
Run describe-vpcs command (OSX/Linux/UNIX) to list the VPC networks available in the current AWS region:
aws ec2 describe-vpcs
02
The command output should expose each VPC ID and its metadata:
{
"Vpcs": [
{
"VpcId": "vpc-f7ac5792",
"InstanceTenancy": "default",
"Tags": [
{
"Value": "MyWebVPC",
"Key": "Name"
}
],
"State": "available",
"DhcpOptionsId": "dopt-80e3f7e2",
"CidrBlock": "172.31.0.0/16",
"IsDefault": true
}
]
}
03
Run describe-flow-logs command (OSX/Linux/UNIX) using the VPC ID to determine if the selected virtual network has the Flow Logs feature enabled:
aws ec2 describe-flow-logs --filter "Name=resource-id,Values=vpc-f7ac5792"
04
If there are no Flow Logs created for the selected VPC, the command output will return an empty list []:
{
"FlowLogs": []
}
01
Sign in to the AWS Management Console.
02
Navigate to VPC dashboard at https://console.aws.amazon.com/vpc/.
03
In the left navigation panel, select Your VCPs.
04
Select the VPC that you need to check.
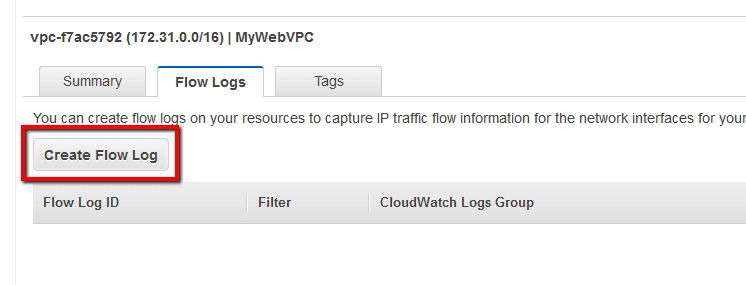
06
In the Create Flow Log dialog box, enter the following details:
- Filter: select the filter that describes the type of traffic to be logged - accepted, rejected, or all.
- Role: enter the name of the IAM role that will allow permissions to publish to the CloudWatch Logs log group.
- Destination Log Group: enter a name for the new CloudWatch Logs log group, where the flow logs will be published.
07
Review the flow log configurationCreate Flow Log:
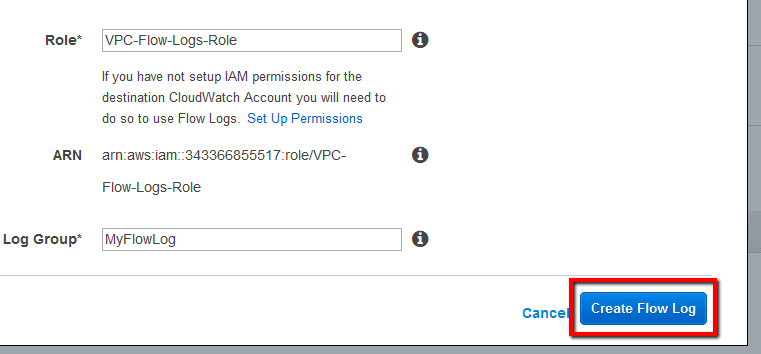
The log group will be available in approximately 10 minutes after you create the flow log. To access it, just click on the log group name listed under the CloudWatch Logs Group column:
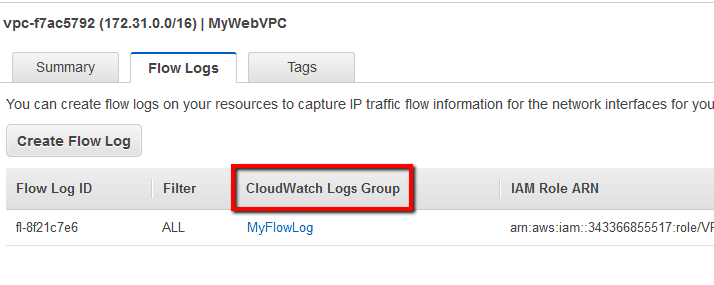
Or open the CloudWatch Logs dashboard at
https://console.aws.amazon.com/cloudwatch/home#logs01
Run create-flow-logs command (OSX/Linux/UNIX) to create a flow log for the selected VPC, in the current AWS region. The following example creates a flow log that captures all traffic for the VPC network with the ID vpc-f7ac5792. The flow logs are delivered to a log group called MyFlowLogs, using an IAM role named VPC-Flow-Logs-Role:
aws ec2 create-flow-logs
--resource-type VPC
--resource-ids vpc-f7ac5792
--traffic-type ALL
--log-group-name MyFlowLogs
--deliver-logs-permission-arn arn:aws:iam::123456789012:role/VPC-Flow-Logs-Role
02
The command output should return the new flow log ID:
{
"Unsuccessful": [],
"FlowLogIds": [
"fl-272ec84e"
],
"ClientToken": "fXBO2YJj/485asmdXnhIw1ycw6ZpTlRxJkhQMyFKygY="
}
03
Run describe-flow-logs command (OSX/Linux/UNIX) using the VPC ID to determine if the selected virtual network has the Flow Logs feature enabled:
aws ec2 describe-flow-logs --filter "Name=resource-id,Values=vpc-f7ac5792"